moofPatch
Set it and forget it! Automatic 3rd-party app updates for all Macs, every 2 or 4 weeks.
Introduction
moofPatch is an automated solution that enforces updates for 3rd party applications on macOS. The service leverages the built-in capabilities of MDM solutions, adding enforcement of updates for security compliance, whilst minimising user disruption via deferral options, smart logic for meeting room apps and clear feedback to the user when patching occurs.
All updates and MDM related config are maintained by Moof IT, following a strict testing and release process that minimises the risk of disruption.

Patching process
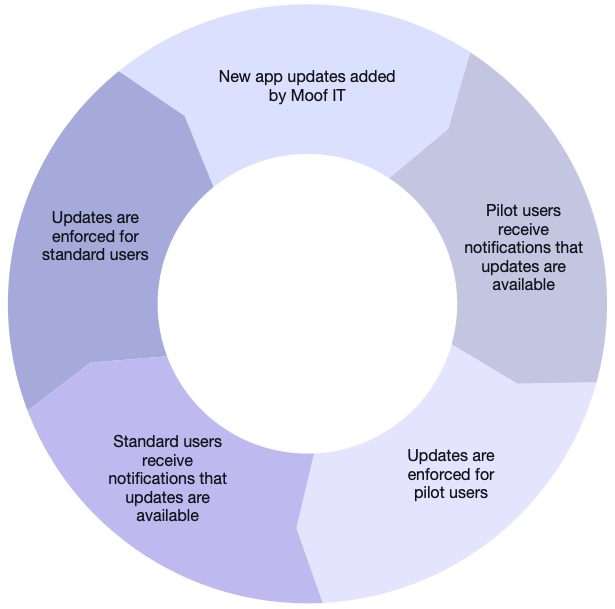
The following process is either 14 or 28 days in duration, depending on your chosen patch cycle:
- On day 1 of the patching cycle, Moof will add available updates for all agreed applications to your MDM solution
- On day 2, your pilot users will start to receive notifications that updates are available, including the date at which they will be enforced, if they choose to defer them
- On the agreed enforcement date, pilot users will have any available app updates enforced
- The following day, all remaining users will start to receive notifications that updates are available
- On the final enforcement day, all remaining users (that haven’t chosen to run them already), will have the updates enforced on their Macs
Key features
Enforced app updates
All apps included in your moofPatch config are subject to enforced updates on the organisation Macs, ensuring the devices stay up to date with bug fixes and compliant with security accreditations.
Pilot and standard user phased rollout approach
Update rollouts are phased with pilot users first, followed by your main Mac user group. This helps to ensure any more subtle bugs in specific app updates are detected before being deployed to all users.
14 or 28 day patching schedules
Your organisation has the option of enforcing either a 28-day or 14-day patching cycle, allowing you to adhere to any security accreditations that require a stricter patching frequency such as Cyber Essentials +.
Ad-hoc critical patch enforcement
In cases where a critical app update is identified, moofPatch allows the addition of ad-hoc updates being flagged as “critical”. This enforces the installation of the update for the affected Mac within 24 hours, independently from the main patching cycle.
Please note that Moof are not responsible for monitoring devices for vulnerable software. Notification of a critical patch would need to be provided by your vulnerability management team.
If required, Moof are able to provide vulnerability management as a service, integrated with moofPatch for automatic addition of critical vulnerability patches.
Online meeting awareness
moofPatch is aware of meeting room software (including Zoom, Microsoft Teams, Webex & GoToMeeting) and detects whether a meeting is in progress. This allows you to run moofPatch safely on your devices knowing that it won’t enforce updates if a user is in an online meeting.
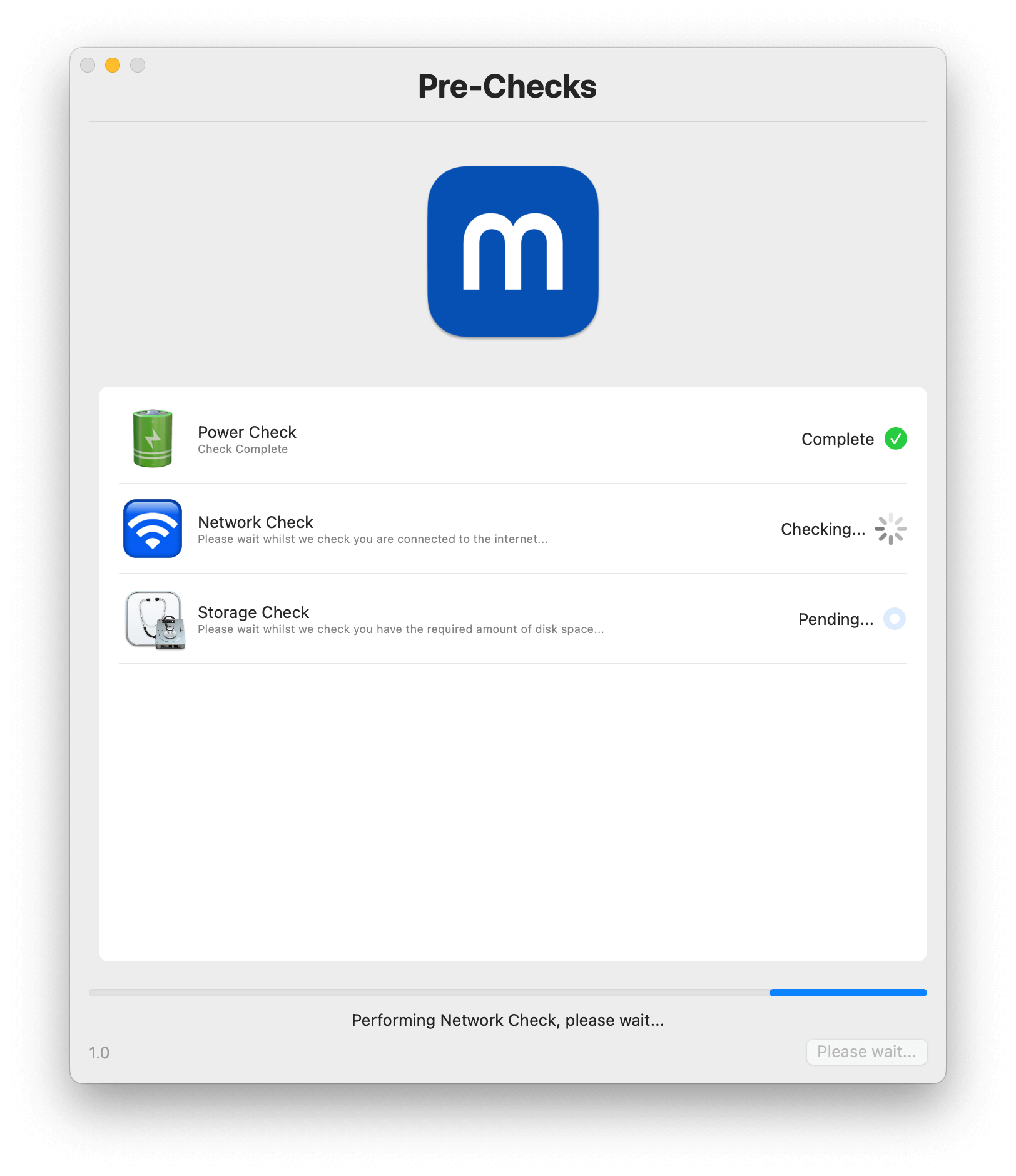
Pre-patching device check
To help ensure a smooth deployment of app updates, moofPatch automatically checks for power, network and disk space, flagging up any issues for review if required:
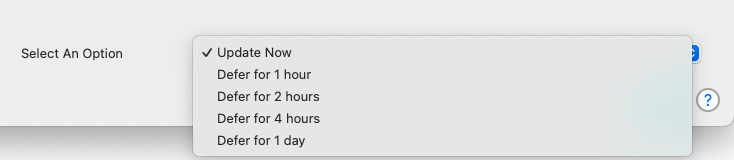
Customisable patching deferral options
When moofPatch starts alerting users about pending software updates, they can be presented with a range of options including “Run updates now”, “Defer for X amount of time” or “Defer notifications until the enforcement time”.
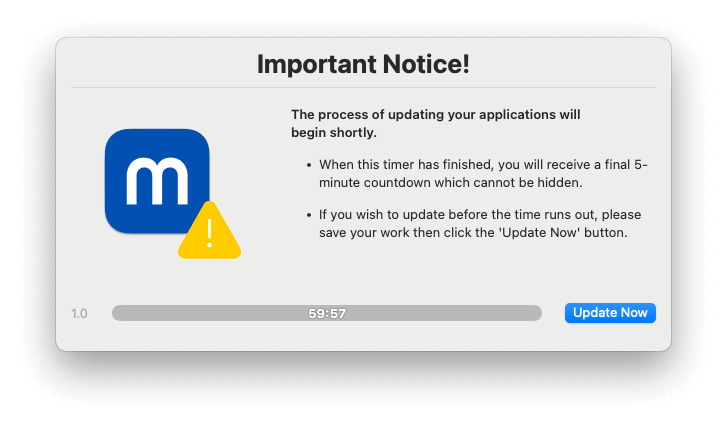
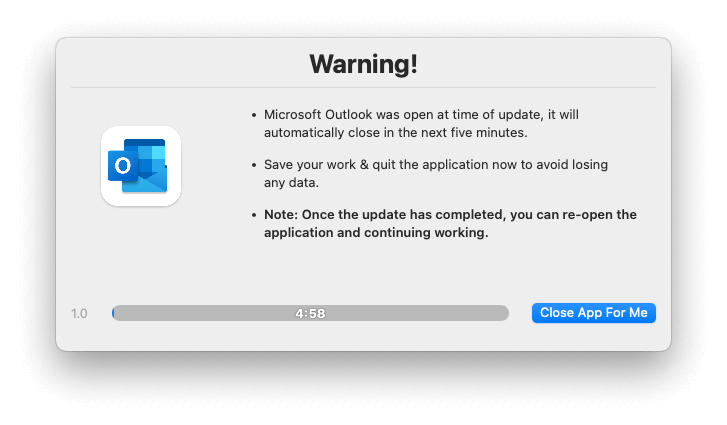
Automatic application closing
moofPatch is configured to automatically close any open apps before they are patched. This helps ensure that the overall update process is successful as possible and avoids application corruption. In these cases, users are notified and given a 5-minute countdown to allow them to save any open work:
Options
Below are the configurable options available for moofPatch. In each case, Moof have a default selection (noted below), but please let us know if you would like to customise the system further:
Required – Patching cycle of 14 or 28-days
- Default behaviour: 28-days
Required – Pilot and Standard users
Devices can be marked as either “pilot” or “standard”. Pilot users will have updates enforced ahead of standard users, allowing them to provide feedback if required, or to flag any potential issues that require the update rollout to be paused.
Moof would recommend approximately 5% of your devices be marked as pilots, up to 20-30 devices in the case of larger Mac estates.
Hide Updates Until After Pilot Deadline
This option hides any available updates from standard users until after the pilot Macs have completed them.
- Default behaviour: Disabled
Deferral time options (e.g. 1 hour, 4 hours, 1 day, 2 days etc)
This setting allows you to specify which deferral options will be available to users in your organisation:
- 1 Hour (Default)
- 2 Hours (Default)
- 4 Hours (Default)
- 8 Hours (Default)
- 1 Day (24 Hours) (Default)
- 2 Days (48 Hours)
- 5 Days (120 Hours)
- Defer until Deadline
Defer until Deadline option
This setting adds an extra deferral option for users to defer all notifications until the patching deadline. Please note that if selected, the user will receive no further reminders about updates until they are enforced on the device.
Meeting & Presentation App Deadline Behaviour
You can choose from the following three options when an update is required for online meeting software:
- Complete Updates even if a meeting is in progress
- Complete Updates but skip in progress meeting and/or presentation apps. (Default)
- Skips all updates if a meeting and/or presentation app is in progress
Custom Patch Deadline
This option allows you to override the standard deadline and specify the amount of days users have until updates are forced (between 3 & 14 days).
- Default behaviour: Disabled
FAQs
Can users skip certain updates or do they have to apply all updates at once?
When users either make the choice to update or have reached a deadline, they will need to apply all updates at once.
Can a user run updates as soon as they are available, rather than waiting for the enforcement deadline?
Yes, a user is able to run updates at any time before the deadline for a greater degree of autonomy and control over when they are applied.
Can we exclude certain users from the enforcement deadline?
The patching behaviour is uniform for all devices within scope and cannot have exceptions to allow users to not be enforced whilst ensuring updates are available.
Therefore the only options for devices/groups is moofPatch enabled or disabled.
Please note that if you chose to exclude devices from patching, Moof recommend you ensure you have an alternative routine maintenance action scheduled to keep those Macs up to date & compliant.
What happens if a user is in a meeting when moofPatch runs?
There are two distinct scenarios to consider for this situation:
- If a user has not yet reached the deadline and a meeting is currently in progress when moofPatch runs, moofPatch will silently exit and reschedule for an hour when the user is no longer engaged in a meeting. Consequently, the user will not receive any notifications during this period.
- If a user has indeed reached a deadline, the behaviour specified under the ‘Meeting & Presentation App Deadline Behaviour’ key will be implemented accordingly.
Does moofPatch update applications as soon as there is a new update released?
No, we offer a managed service which works though ‘patching cycles’ of 14 or 28 days. This consistent approach ensures users are only enforced to patch once within that given timeframe and reduce the amount of notifications users receive.
The additional benefits of using ‘patching cycles’ is your pilot users join hundreds of other pilot users from multiple businesses across a vast array of industries who are all testing the same packages at the same time. This approach further strengthens our capacity to test and address troublesome updates within live environments effectively before the updates are released to the rest of your user base.
If a new update is released, will it be added to the current running patch cycle?
It will not. Any new updates released after the start of your current patch cycle will be added to the next patch cycle by default. The exception will be if you notify us of a critical security patch, which can be handled separately.
What if a critical security update is released by a vendor?
If there is a critical security update released by a vendor, you can notify Moof IT and we can add it to your current patch cycle. We will mark the update as “critical”, which will require users to install it within 24 hours, regardless of their pilot/standard user status.
Can I customise the text shown in the messages?
Unfortunately not, moofPatch utilises markdown for formatting features such as tables, bold text, headings, bullet points, and more. We are actively exploring options to enable customers to personalise their messages without affecting the functionality of the moofPatch solution. While it’s unlikely that full customisation of all messages will be feasible, we aim to offer the ability to designate specific sentences or incorporate support contact information in the future.
How do I report bugs or issues with moofPatch?
Please log a ticket with Moof IT.
Can I make a feature request for moofPatch?
Customer feedback is highly valued and integral to our continuous improvement process. The feature suggestion will be carefully considered, and if deemed actionable, will be incorporated into our development. It’s important to note, however, that while we strive to accommodate all requests, we cannot guarantee the approval of every feature submission.



