Number of devices
25,357
Number of projects delivered
937
CSAT score
97.8%
Why work with Moof?
Security & Compliance experts
Tailored security & patching solutions to ensure your devices stay safe.
Moof make it easy
Custom macOS configurations to
deliver on your organisation needs.
End to end Jamf Pro
support
Ongoing support services and
solutions to meet your organisations requirements.
End-to-end Mac Management
& support from Moof IT
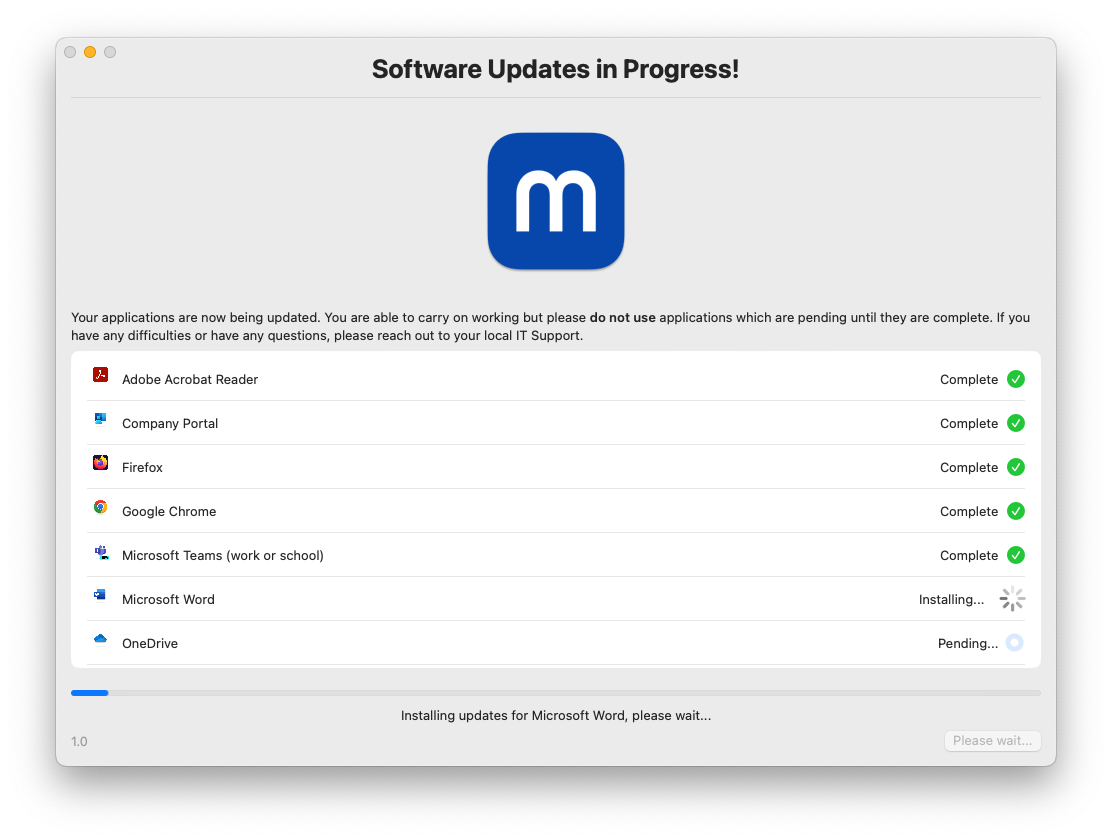
moofPatch
Automated Mac
patching solution
Automated patching solution which updates all third-party applications in a single enforced regular event.
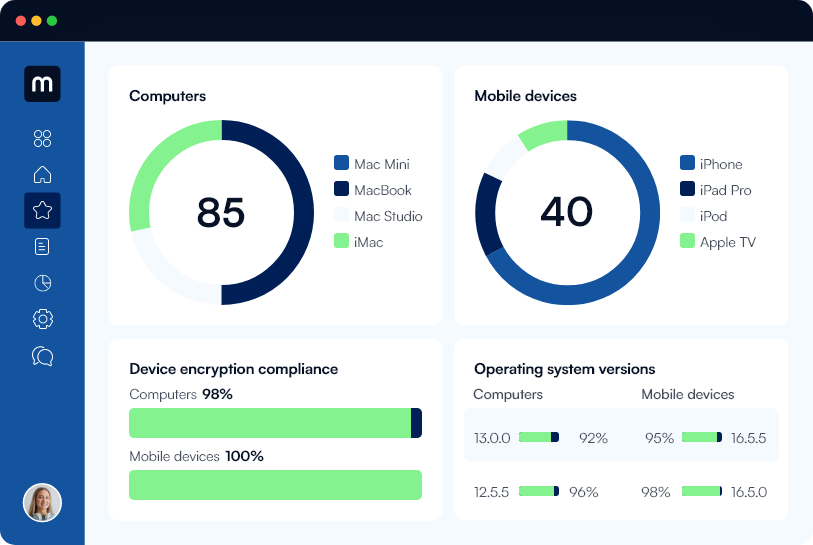
moofSecure
All your systems
fully secure and compliant
Go beyond conventional security measures and ensure your systems are fully compliant with industry standards and regulations.
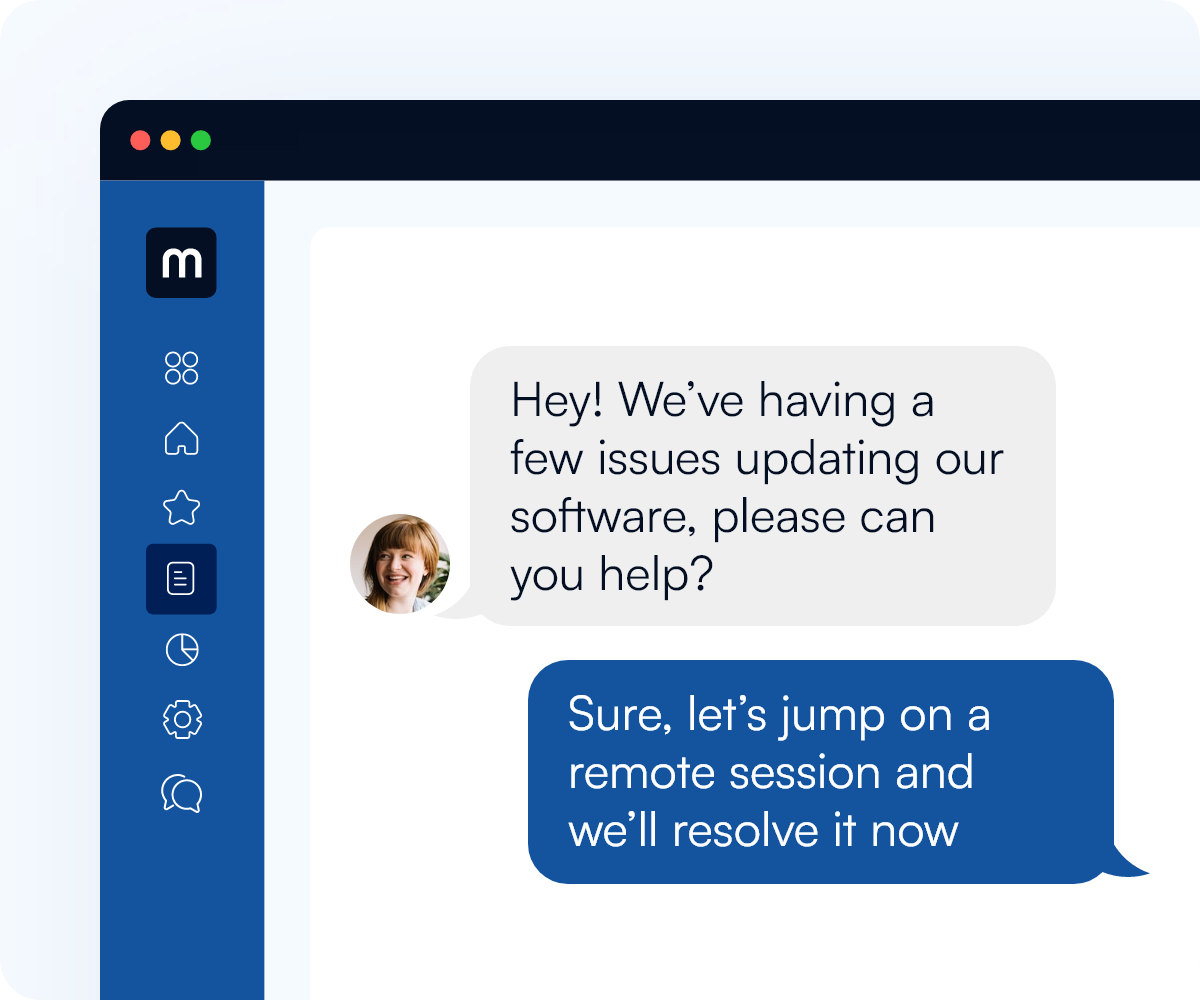
macOS Support
Specialists in macOS support
Have your organisations Mac devices supported by our knowledgeable, proactive London based IT support team. With over 150 years collective IT support experience supporting both internal IT teams and users directly, we will ensure your employees get back to what is important ASAP.
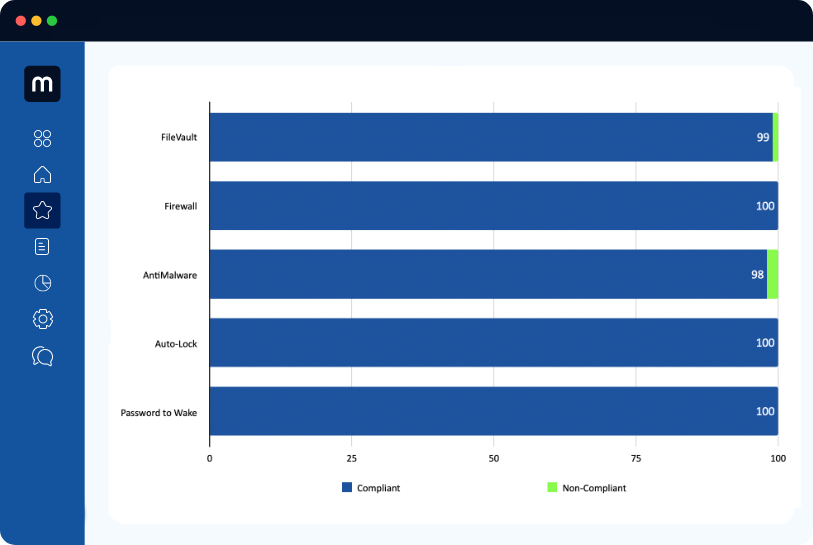
Reporting
Comprehensive monthly reporting
Stay in control and make informed decisions about your operations with actionable insights into your system’s performance.
Our areas of specialisation
Jamf Pro
Moof use Data analysis and visualisation tools to better equip our experienced technical team to deliver outstanding Jamf-focused services.
Education
Moof started their journey in Apple device management in education over 18 years ago. We are now extremely proud to provide Apple & Jamf Pro support to over 30 Universities and colleges in the UK and abroad.

User support
Moof IT provide fully managed IT support and escalated macOS support to over 60+ UK companies from our main office in Soho, London.





